The presence of a cloud security expert is essential in your IT department. If you haven’t already, it’s time to have them sit at the table and listen to their voice for robust security implementation. Why? The cyber security landscape has changed dramatically over the past several years, and what used to work no longer works. Even worse, it may look like it still works. Until it really, really happens. Let’s break it down: Traditional cyber security uses a perimeter-based model. Under this model, apps weren’t built with as many independent, integrated security features as they didn’t need to be. They could rely on the perimeter.
Today, the landscape is increasingly cloud-based. In some cases, the perimeter is still there (think local firewalls), but because cloud-native apps are designed to run anywhere on any server – and are highly connected – perimeter security is no longer the be-all and end-all.
The mobility, agility, and flexibility of modern containerized apps give them tremendous value and make them suitable for the remote workforce. Problems arise when traditional cyber security rules are applied to a cloud-native landscape. And the gap between modern cloud-native apps and traditional security is widening. Apps are being engineered and deployed in this new landscape, and then — because apps aren’t limited to a defined, secure perimeter — IT is expected to layer on security later. The best or reactionary step is to take after security is already a problem. But there’s a better plan: Bring in security experts during the design phase and build an app that’s agile and flexible, meets zero-trust goals, and is in line with the design. That’s all to say: DevOps needs to become DevSecOps.
Where Does DevSecOps Implement?
The key to both DevOps and DevSecOps is automation. Automation ensures that the required steps are performed each time the code is pushed and eliminates human intervention. For many, it can be difficult to identify opportunities about where and how to automate security testing in a development pipeline. Here are five areas where DevSecOps must be implemented into the development pipeline to benefit from security testing automation.
1. SAST/DAST
Since DevSecOps is about adding security first in development and operations, adding SAST/DAST into the DevOps pipeline helps build a sustainable program and automate for efficiency, consistency, and early detection of vulnerabilities. SAST or Static Application Security Testing allows developers to find security vulnerabilities in application source code earlier in the software development lifecycle. It also ensures to conform to coding guidelines and standards without executing the underlying code. On the other hand, DAST, or Dynamic Application Security Testing, helps find security vulnerabilities in a running application, usually a web app. Integrating SAST/DAST into DevOps processes helps identify, plan solutions, and fix issues like managing false positives, triaging the results, having a plan ready to cope with a situation when a new issue is identified, and performing a baseline scan. SAST and DAST as cloud security capabilities serve the purpose as a first stage of ensuring application security in DevSecOps practices.
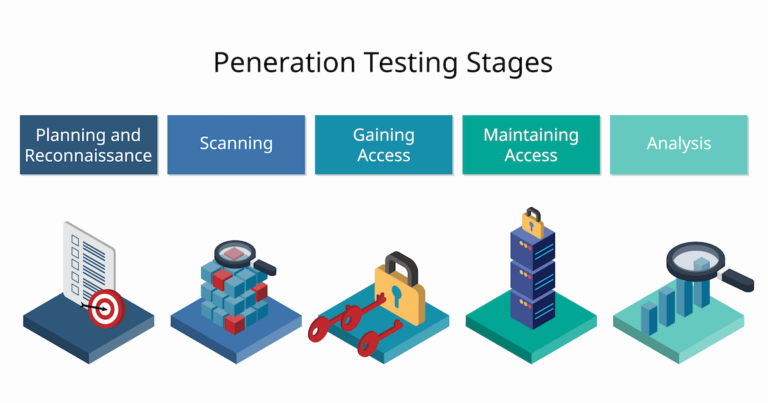
2. Penetration Testing
Penetration testing has become a proactive security measure to build a comprehensive security strategy. It is known to validate security programs and measure the effectiveness of an organization’s patch management and incident response programs for the software and hardware. Traditional pen-testing engagements failed to deliver the speed and flexibility DevSecOps needed. Considering the needs of DevSecOps teams, Penetration Testing-as-a-Service (PTaaS) is seeing a high profile. Incremental pen-testing programs can help identify and address security vulnerabilities more frequently and help security teams increase reach and accelerate secure build-to-release timelines. There are five stages of penetration testing that are used to identify and exploit security threats.
There are many real-world use cases where penetration testing helps companies ensure system security. Check here how Nokia uses black box penetration testing solutions and addresses and eliminated security issues.
3. Regression
DevOps enables developers to continuously improve applications without disturbing the end user’s experience. DevSecOps uses regression testing to allow developers to discover whether they can introduce new code without worrying about existing functionality. It is used and performed on the entire group of modified applications or in partial sections to ensure critical functionalities don’t fail when an update occurs. When DevSecOps uses regression testing, the diverse use cases include:
- Implementing new code.
- Making changes to old code when an application is ported to another platform.
- Addressing program bugs.
- Fixing performance issues and others are included.
4. Container Scanning
IBM Systems Sciences Institute once found that the cost of fixing defects during the maintenance phase (i.e., runtime) was 100 times more costly than identified during design. The rapid adoption of containers in an enterprise represents a unique opportunity to shift security left and move a step closer to DevSecOps processes. Since dependencies are grouped in containers that require less work from an operational standpoint, the temptation may be to forget about those vulnerabilities or not realize they exist. Being ignorant of security or vulnerabilities often leads to breaches through containers. The vital components that can be impacted to break into your system are container repositories, container images, and runtime.
Scanning Container Images: Security teams should integrate image scanning into their CI/CD pipeline to detect and block vulnerabilities before their code enters the container. Continuous scanning of the container registry where all your application images are stored is crucial for maintaining container security.
Scanning Container Registry: Container registry could be a centralized hub for the container environment or potentially hold crucial for maintaining container security. A single vulnerability or insecure configuration can pose a threat not only to your registry but to your entire application. This function should automatically scan each image to identify and prevent incoming threats.
Scanning Container Runtime: Just because your container is up and running doesn’t mean that your container scanning responsibilities are over. For optimal container security, it is essential to automate continuous scanning that identifies any new CVEs as they are detected. This will help detect new vulnerabilities, report them to your security team, and allow you to take immediate action.
5. Software Composition
With short release cycles, today’s software development landscape leads dev teams to rely heavily on open source to accelerate innovation. However, every open source component involved in an organization’s projects must be tracked to avoid the risk of legal non-compliance and to maintain a strong security posture. In a DevSecOps environment, this tracking must be integrated at each development lifecycle stage. Implementing DevOps quality gates in CI/CD pipeline is also an effective way to ensure application security as it addresses the issues early and doesn’t allows bugs or issues to be passed to the next phase of development.
Software Structure Analysis (SCA) provides visibility into the inclusion of open-source components and libraries into software that comprises the development team. SCA can help manage security and licensing-related risks. This can help ensure that any open-source components embedded in applications meet specific standards to avoid risks that could lead to data breaches, compromised intellectual property, or legal disputes. Software architecture analysis provides excellent help for open-source vulnerability management and open-source license management.
Conclusion
DevSecOps incorporates security practices into the development process, enabling teams to identify and address security vulnerabilities early on and continuously monitor for threats in production. DevSecOps provides cloud security capabilities such as improving overall security and compliance, while also enabling organizations to quickly respond to emerging threats and compliance requirements.