Tag: Cybersecurity
Cloud Security and DevSecOps

Difference Between Internal Vs External Penetration Testing
Information of any kind has been crucial since ages and keeping them secret remains a tough job since then. In today’s digital world, when someone mentions ‘data protection’, they mean securing information be it people’s personal information or financial data or sensitive business information like intellectual properties, business strategies, employee…
Learn MoreCloud Security and DevSecOps

How DevSecOps Keep The Application Secure
The presence of a cloud security expert is essential in your IT department. If you haven’t already, it’s time to have them sit at the table and listen to their voice for robust security implementation. Why? The cyber security landscape has changed dramatically over the past several years, and what…
Learn MoreCloud Security and DevSecOps
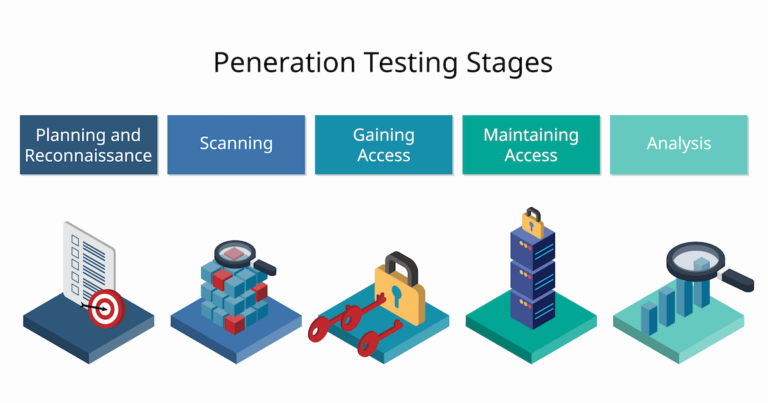
Penetration Testing Phases: A Roadmap To Secure Enterprise Applications
All Internet-facing systems and applications carry security risks. Any application with ineffective security controls in place is potentially vulnerable. Attackers target e-commerce sites, third-party service providers, mobile applications, network applications, and other companies that provide applications used on websites. Cybercrime and similar threat actors continue evolving and modifying their attacks,…
Learn MoreApplication Modernization
Why Do Enterprises Need Application Modernization?
In the early days of the evolution of technologies, enterprises adopted digital transformation as a survival mechanism. Sooner or later, companies realized digital transformation is a never-ending process. Instead of considering it a survival strategy, digital transformation has been viewed as a continuous improvement serving varied business objectives. Therefore, enterprises…
Learn MoreSRE as a Service

How To Plan Preventive Maintenance For Networks And Servers
Businesses rely heavily on their networks and servers, and regular server maintenance must be performed to keep them functional. Preventive maintenance keeps servers running as expected and allows businesses to operate smoothly and avoid downtime or loss of data. This includes reviewing server performance, ensuring that automated system monitoring utilities…
Learn MoreMarket Insights

Top Emerging Cyber Security Trends to Watch in 2022
Today, companies have data, substantial assets, and information exhibited in digital form and they are increasingly relying on digital systems to manage their day-to-day activities. Global pandemic started in 2020 has been favorable for cyber criminals as remote working, the on-going digitization of services create huge opportunities for them, and…
Learn MoreCloud Security and DevSecOps

Maintaining Cyber Security In The Remote Work Environment
Remote work and hybrid offices are the new normal. We all know this shift in the workplace is a result of global pandemic. While employees find work from home culture convenient and ask for better policies from employers, organizations are struggling with new challenges posed by cyber security in remote…
Learn MoreCloud Security and DevSecOps

Understanding Endpoint Security and Its Importance in an Enterprise
Endpoint security is a cybersecurity practice performed to secure endpoints such as desktops, laptops, servers, and fixed-function devices from all types of malicious acts that could be triggered from internal or external sources. Endpoints are connected through a network and can communicate with other points and devices across the network.…
Learn MoreCloud Security and DevSecOps

Multitenant Security In Cloud Computing
Multitenant architecture, commonly referred to as multitenancy, is about designing systems in such a manner that they are “shared.” It is a core tenant of cloud computing and offers substantial benefits to cloud service providers, organizations, and end-users. It has taken the cloud computing model beyond efficiency and cost optimization.…
Learn MoreCloud Security and DevSecOps

What is operational security? Proven steps to achieve OpSec in an IT
A company could have a threat in many ways, or its security could be breached by anyone, including an employee, former employee, contractor, business associate, or other organization members who have access to critical data and IT systems. Even the ids and identities of a current employee could be tweaked…
Learn More