Category: Cloud Security and DevSecOps
Cloud Security and DevSecOps

How To Secure Healthcare Data On Cloud?
The healthcare sector generates and manages extensive volumes of sensitive data critical to ensuring quality patient care and positive health outcomes. However, with the introduction of eHealth applications in an already complex and data-rich environment, healthcare organizations are facing new challenges. They must swiftly adapt to support more patients, comply…
Learn MoreCloud Security and DevSecOps

Difference Between Internal Vs External Penetration Testing
Information of any kind has been crucial since ages and keeping them secret remains a tough job since then. In today’s digital world, when someone mentions ‘data protection’, they mean securing information be it people’s personal information or financial data or sensitive business information like intellectual properties, business strategies, employee…
Learn MoreCloud Security and DevSecOps

How DevSecOps Keep The Application Secure
The presence of a cloud security expert is essential in your IT department. If you haven’t already, it’s time to have them sit at the table and listen to their voice for robust security implementation. Why? The cyber security landscape has changed dramatically over the past several years, and what…
Learn MoreCloud Security and DevSecOps
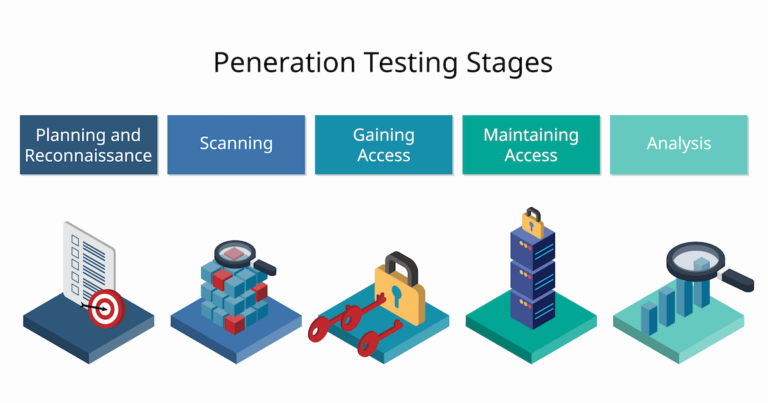
Penetration Testing Phases: A Roadmap To Secure Enterprise Applications
All Internet-facing systems and applications carry security risks. Any application with ineffective security controls in place is potentially vulnerable. Attackers target e-commerce sites, third-party service providers, mobile applications, network applications, and other companies that provide applications used on websites. Cybercrime and similar threat actors continue evolving and modifying their attacks,…
Learn MoreCloud Security and DevSecOps

How Secure Is Your Serverless Architecture: Security Risks & Best Practices
Serverless architectures take the need to manage infrastructure-related operations out of the equation and allows the organizations and their application developers to focus more on developing quality code. This model of computing brings a myriad of benefits like faster deployment, increased flexibility, scalability and accessibility. No need to worry about…
Learn MoreCloud Security and DevSecOps

Maintaining Cyber Security In The Remote Work Environment
Remote work and hybrid offices are the new normal. We all know this shift in the workplace is a result of global pandemic. While employees find work from home culture convenient and ask for better policies from employers, organizations are struggling with new challenges posed by cyber security in remote…
Learn MoreCloud Security and DevSecOps

Understanding Endpoint Security and Its Importance in an Enterprise
Endpoint security is a cybersecurity practice performed to secure endpoints such as desktops, laptops, servers, and fixed-function devices from all types of malicious acts that could be triggered from internal or external sources. Endpoints are connected through a network and can communicate with other points and devices across the network.…
Learn MoreCloud Security and DevSecOps

Multitenant Security In Cloud Computing
Multitenant architecture, commonly referred to as multitenancy, is about designing systems in such a manner that they are “shared.” It is a core tenant of cloud computing and offers substantial benefits to cloud service providers, organizations, and end-users. It has taken the cloud computing model beyond efficiency and cost optimization.…
Learn MoreCloud Security and DevSecOps

What is operational security? Proven steps to achieve OpSec in an IT
A company could have a threat in many ways, or its security could be breached by anyone, including an employee, former employee, contractor, business associate, or other organization members who have access to critical data and IT systems. Even the ids and identities of a current employee could be tweaked…
Learn MoreCloud Security and DevSecOps
Data Security: How To Keep Data Secure In The Cloud?
Data security is the amalgamation of best practices and the technology of protecting valuable and sensitive company and customer data, for instance, personal or financial information. Every business now collects, stores, and manages valuable data in the cloud. Hackers look for sensitive information in the cloud-based applications such as the…
Learn MoreCloud Security and DevSecOps

Top 12 Cloud Security Best Practices
Cloud security refers to using technologies, processes, controls, policies and combining them all to protect cloud-based systems, data and infrastructure. Though it is considered a sub-domain of computer security and more broadly comes under information security, as data is stored on the cloud, security posture changes with which customers and…
Learn MoreCloud Security and DevSecOps
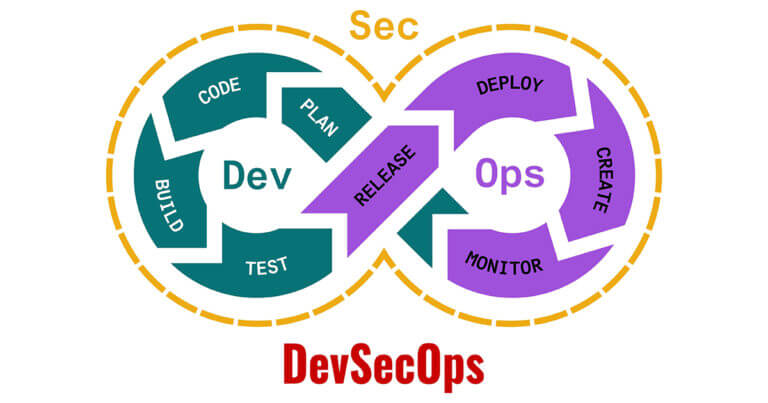
What Is DevSecOps And Why Is It Important In DevOps Mix?
In recent years, DevOps as a development process has gained traction and popularity for providing the opportunity to outperform the competition through continuous innovation and meeting customer needs. Although this development methodology brings together development and operations teams to work across the entire application lifecycle to speed up delivery and…
Learn More